Istio 1.0学习笔记(一):在Kubernetes安装Istio
📅 2018-08-22 | 🖱️
🔖 istio
Istio已经发布了可以用于生产的1.0版本,这里也跟进一下。首先,我们需要在Kubernetes上安装Istio,这里将实验基于安装包安装方式。 本文的实验环境是Kubernetes 1.11。
istio的文档中说istio 1.0需要Kubernetes 1.9或更高版本,需要Kubernetes的CRD(自定义资源定义)功能
1.使用Istio安装包安装 #
1.1 下载Istio发布包 #
下载并解压缩istio的发布包:
1wget https://github.com/istio/istio/releases/download/1.0.0/istio-1.0.0-linux.tar.gz
2tar -zxvf
3cd istio-1.0.0
解压缩后的目录结构如下:
1├── istio-1.0.0
2│ ├── bin
3│ │ └── istioctl
4│ ├── install
5│ │ ├── consul
6│ │ ├── gcp
7│ │ ├── kubernetes
8│ │ ├── README.md
9│ │ └── tools
10│ ├── istio.VERSION
11│ ├── LICENSE
12│ ├── README.md
13│ ├── samples
14│ │ ├── bookinfo
15│ │ ├── certs
16│ │ ├── CONFIG-MIGRATION.md
17│ │ ├── health-check
18│ │ ├── helloworld
19│ │ ├── httpbin
20│ │ ├── https
21│ │ ├── kubernetes-blog
22│ │ ├── rawvm
23│ │ ├── README.md
24│ │ ├── sleep
25│ │ └── websockets
26│ └── tools
27│ ├── cache_buster.yaml
28│ ├── convert_perf_results.py
29│ ├── deb
30│ ├── dump_kubernetes.sh
31│ ├── githubContrib
32│ ├── hyperistio
33│ ├── istio-docker.mk
34│ ├── license
35│ ├── perf_istio_rules.yaml
36│ ├── perf_k8svcs.yaml
37│ ├── perf_setup.svg
38│ ├── README.md
39│ ├── rules.yml
40│ ├── run_canonical_perf_tests.sh
41│ ├── setup_perf_cluster.sh
42│ ├── setup_run
43│ ├── update_all
44│ └── vagrant
- 其中install/kubernetes目录中包含了在k8s集群上部署Istio的.yaml文件
- bin目录中的istioctl是istio的客户端文件,用来手动将Envoy作为sidecar proxy注入,以及对路由规则和策略的管理
将istioctl加入到PATH环境变量,这里直接将其拷贝到/usr/local/bin下.
1cp bin/istioctl /usr/local/bin
2
3istioctl version
4Version: 1.0.0
5GitRevision: 3a136c90ec5e308f236e0d7ebb5c4c5e405217f4
6User: root@71a9470ea93c
7Hub: gcr.io/istio-release
8GolangVersion: go1.10.1
9BuildStatus: Clean
1.2 安装istio的CRD #
安装istio的CRD(Custom Resource Definitions ),并等待一段时间CRDs将被提交到kube-apiserver中:
1kubectl apply -f install/kubernetes/helm/istio/templates/crds.yaml
查看安装的CRD:
1kubectl get CustomResourceDefinition
1.3 安装Istio的核心组件 #
安装istio核心文件并不启用sidecar之间的TLS双向认证:
1kubectl apply -f install/kubernetes/istio-demo.yaml
1.4 验证安装 #
确认istio相关的Service已经部署:
1kubectl get svc -n istio-system
确认istio相关的Pod都处于running状态:
1kubectl get pod -n istio-system
2NAME READY STATUS RESTARTS AGE
3grafana-86645d6b4d-j56qg 1/1 Running 0 12m
4istio-citadel-55d9bb9b5f-9x5s2 1/1 Running 0 12m
5istio-cleanup-secrets-lvqlg 0/1 Completed 0 12m
6istio-egressgateway-74bbdd9669-wsdhb 1/1 Running 0 12m
7istio-galley-d4bc6c974-97h5n 1/1 Running 0 9m
8istio-grafana-post-install-hn5w4 0/1 Completed 0 12m
9istio-ingressgateway-756584cc64-9wqsx 1/1 Running 0 12m
10istio-pilot-7dd78846f5-qbcrq 2/2 Running 0 12m
11istio-policy-b9d65465-c2jc6 2/2 Running 0 12m
12istio-sidecar-injector-854f6498d9-22lb8 1/1 Running 0 10m
13istio-statsd-prom-bridge-549d687fd9-6lfll 1/1 Running 0 12m
14istio-telemetry-64fff55fdd-tx99p 2/2 Running 0 12m
15istio-tracing-7596597bd7-5m24x 1/1 Running 0 11m
16prometheus-6ffc56584f-mrqpk 1/1 Running 0 12m
17servicegraph-7bdb8bfc9d-xldll 1/1 Running 0 12m
1.5 卸载Istio #
1kubectl delete -f install/kubernetes/istio-demo.yaml
2
3kubectl delete -f install/kubernetes/helm/istio/templates/crds.yaml -n istio-system
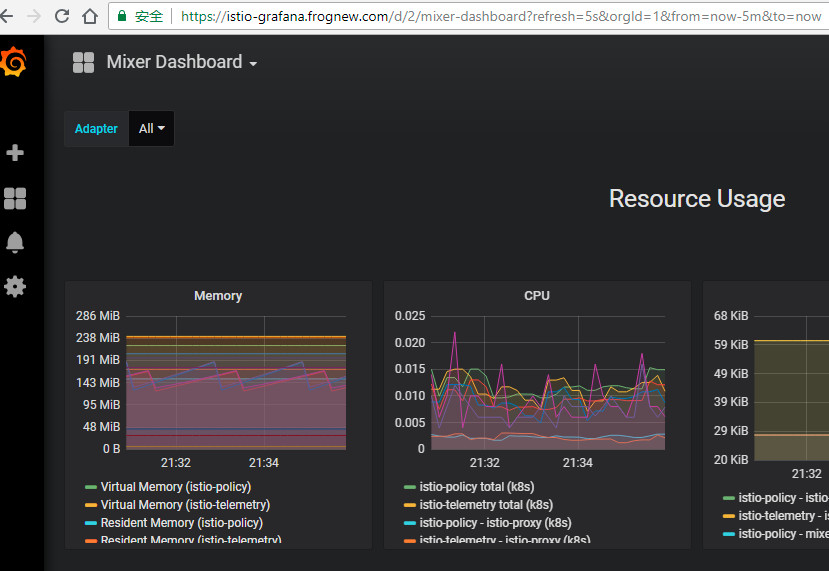
2.grafana和jaeger #
通过查看istio-system命名空间中的svc和pod,我们看到istio的安装还包含了Prometheus、Grafana、Jaeger,我们先使用ingress将这三个服务的WebUI暴露到集群外边:
这里使用的已经部署在Kubernetes中的ingress nginx将这个三个服务暴露到集群外部,而没有使用Istio Gateway,关于Istio Gateway的功能我们后边单独学习
将站点的SSL证书存放到istio-system命名空间中:
1kubectl create secret tls frognew-com-tls-secret --cert=fullchain.pem --key=privkey.pem -n istio-system
1---
2apiVersion: extensions/v1beta1
3kind: Ingress
4metadata:
5 name: jaeger-query
6 namespace: istio-system
7 annotations:
8 nginx.ingress.kubernetes.io/ssl-redirect: "true"
9 nginx.ingress.kubernetes.io/secure-backends: "false"
10spec:
11 rules:
12 - host: istio-jaeger.frognew.com
13 http:
14 paths:
15 - path: /
16 backend:
17 serviceName: jaeger-query
18 servicePort: 16686
19 tls:
20 - hosts:
21 - istio-jaeger.frognew.com
22 secretName: "frognew-com-tls-secret"
23
24---
25apiVersion: extensions/v1beta1
26kind: Ingress
27metadata:
28 name: prometheus
29 namespace: istio-system
30 annotations:
31 nginx.ingress.kubernetes.io/ssl-redirect: "true"
32 nginx.ingress.kubernetes.io/secure-backends: "false"
33spec:
34 rules:
35 - host: istio-prometheus.frognew.com
36 http:
37 paths:
38 - path: /
39 backend:
40 serviceName: prometheus
41 servicePort: 9090
42 tls:
43 - hosts:
44 - istio-prometheus.frognew.com
45 secretName: "frognew-com-tls-secret"
46
47---
48apiVersion: extensions/v1beta1
49kind: Ingress
50metadata:
51 name: grafana
52 namespace: istio-system
53 annotations:
54 nginx.ingress.kubernetes.io/ssl-redirect: "true"
55 nginx.ingress.kubernetes.io/secure-backends: "false"
56spec:
57 rules:
58 - host: istio-grafana.frognew.com
59 http:
60 paths:
61 - path: /
62 backend:
63 serviceName: grafana
64 servicePort: 3000
65 tls:
66 - hosts:
67 - istio-grafana.frognew.com
68 secretName: "frognew-com-tls-secret"
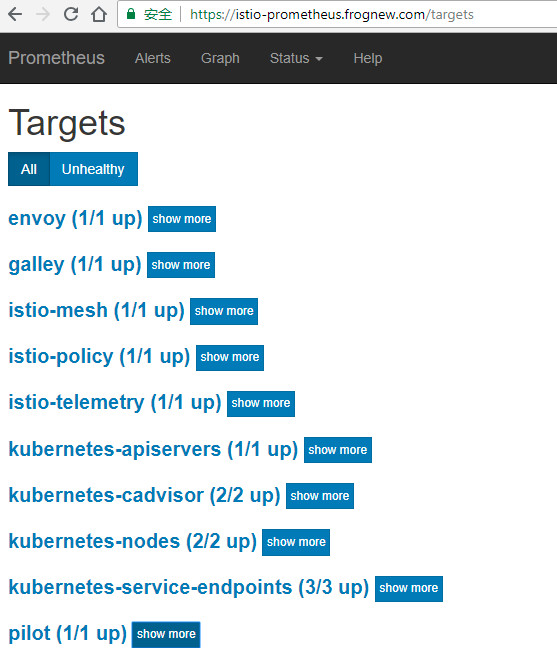
从Prometheus的targes中可以看到当前Prometheus对Kubernetes、Istio的各个核心组件做了监控。