Ceph对象存储之RGW
📅 2017-02-05 | 🖱️
Ceph RGW简介 #
Ceph RGW(即RADOS Gateway)是Ceph对象存储网关服务,是基于LIBRADOS接口封装实现的FastCGI服务,对外提供存储和管理对象数据的Restful API。 对象存储适用于图片、视频等各类文件的上传下载,可以设置相应的访问权限。目前Ceph RGW兼容常见的对象存储API,例如兼容绝大部分Amazon S3 API,兼容OpenStack Swift API。
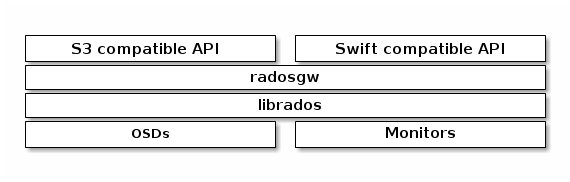
部署Ceph RGW #
Ceph RGW的FastCGI支持多种Web服务器作为前端,例如Nginx、Apache2等。 从Ceph Hammer版本开始,使用ceph-deploy部署时将会默认使用内置的civetweb作为前端。
这里选择和我们线上环境一致的nginx部署,继续使用前面的实验环境:
1192.168.61.30 c0 - admin-node, deploy-node
2192.168.61.31 c1 - mon
3192.168.61.32 c2 - mon osd.1
4192.168.61.33 c3 - mon osd.2
可以把Ceph RGW简单理解成Ceph集群的一个客户端,用户通过它间接的访问Ceph集群,因此我们选择先在实验环境的c1服务器上部署一个RGW节点。
1192.168.61.30 c0 - admin-node, deploy-node
2192.168.61.31 c1 - mon radosgw nginx
3192.168.61.32 c2 - mon osd.1
4192.168.61.33 c3 - mon osd.2
安装ceph-radosgw和nginx #
在c1服务器上安装ceph-radosgw:
1sudo yum install -y ceph-radosgw
在c1服务器上安装nginx,这里采用npm方式安装:
/etc/yum.repos.d/nginx.repo
1[nginx]
2name=nginx repo
3baseurl=http://nginx.org/packages/centos/7/x86_64/
4gpgcheck=0
5enabled=1
1sudo yum install -y nginx
启动nginx,并设置开机启动:
1sudo systemctl start nginx
2sudo systemctl enable nginx
创建RGW用户和keyring #
在c1服务器上创建keyring:
1sudo ceph-authtool --create-keyring /etc/ceph/ceph.client.radosgw.keyring
2sudo chmod +r /etc/ceph/ceph.client.radosgw.keyring
生成ceph-radosgw服务对应的用户和key:
1sudo ceph-authtool /etc/ceph/ceph.client.radosgw.keyring -n client.radosgw.gateway --gen-key
为用户添加访问权限:
1sudo ceph-authtool -n client.radosgw.gateway --cap osd 'allow rwx' --cap mon 'allow rwx' /etc/ceph/ceph.client.radosgw.keyring
导入keyring到集群中:
1sudo ceph -k /etc/ceph/ceph.client.admin.keyring auth add client.radosgw.gateway -i /etc/ceph/ceph.client.radosgw.keyring
创建资源池 #
由于RGW要求专门的pool存储数据,这里手动创建这些Pool,在admin-node上执行:
1ceph osd pool create .rgw 128 128
2ceph osd pool create .rgw.root 128 128
3ceph osd pool create .rgw.control 128 128
4ceph osd pool create .rgw.gc 128 128
5ceph osd pool create .rgw.buckets 128 128
6ceph osd pool create .rgw.buckets.index 128 128
7ceph osd pool create .rgw.buckets.extra 128 128
8ceph osd pool create .log 128 128
9ceph osd pool create .intent-log 128 128
10ceph osd pool create .usage 128 128
11ceph osd pool create .users 128 128
12ceph osd pool create .users.email 128 128
13ceph osd pool create .users.swift 128 128
14ceph osd pool create .users.uid 128 128
列出pool信息确认全部成功创建:
1rados lspools
2......
3.rgw
4.rgw.root
5.rgw.control
6.rgw.gc
7.rgw.buckets
8.rgw.buckets.index
9.rgw.buckets.extra
10.log
11.intent-log
12.usage
13.users
14.users.email
15.users.swift
16.users.uid
RGW配置 #
在c1服务器的/etc/ceph.conf上添加以下内容:
1[client.radosgw.gateway]
2rgw frontends=fastcgi socket_port=9000 socket_host=0.0.0.0
3host=c1
4keyring=/etc/ceph/ceph.client.radosgw.keyring
5log file=/var/log/radosgw/client.radosgw.gateway.log
6rgw print continue=false
7rgw content length compat = true
更多配置查阅CEPH OBJECT GATEWAY CONFIG REFERENCE
nginx配置 #
在/etc/nginx/nginx.conf中http段落中添加如下内容:
1
2server {
3 listen 80 default;
4 server_name c1;
5 location / {
6 fastcgi_pass_header Authorization;
7 fastcgi_pass_request_headers on;
8 fastcgi_param QUERY_STRING $query_string;
9 fastcgi_param REQUEST_METHOD $request_method;
10 fastcgi_param CONTENT_LENGTH $content_length;
11 fastcgi_param CONTENT_LENGTH $content_length;
12 if ($request_method = PUT) {
13 rewrite ^ /PUT$request_uri;
14 }
15 include fastcgi_params;
16 fastcgi_pass 127.0.0.1:9000;
17 }
18 location /PUT/ {
19 internal;
20 fastcgi_pass_header Authorization;
21 fastcgi_pass_request_headers on;
22 include fastcgi_params;
23 fastcgi_param QUERY_STRING $query_string;
24 fastcgi_param REQUEST_METHOD $request_method;
25 fastcgi_param CONTENT_LENGTH $content_length;
26 fastcgi_param CONTENT_TYPE $content_type;
27 fastcgi_pass 127.0.0.1:9000;
28 }
29}
启动RGW #
1sudo mkdir /var/log/radosgw
2sudo chown ceph:ceph /var/log/radosgw
3
4sudo cp /usr/lib/systemd/system/ceph-radosgw@.service /usr/lib/systemd/system/ceph-radosgw@radosgw.gateway.service
5sudo systemctl start ceph-radosgw@radosgw.gateway
6sudo systemctl enable ceph-radosgw@radosgw.gateway
查看radosgw服务状态:
1sudo systemctl status [email protected]
2....
3[/usr/lib/systemd/system/[email protected]:17] Unknown lvalue 'TasksMax' in section 'Service'
报了Unknown lvalue ‘TasksMax’ in section ‘Service’的错误,升级systemd:
1sudo yum install systemd-*
重启再次查看状态,没有问题了:
1sudo systemctl restart [email protected]
2sudo systemctl status [email protected]
1ps -ef | grep radosgw
2ceph 3344 1 1 22:41 ? 00:00:00 /usr/bin/radosgw -f --cluster ceph --name client.radosgw.gateway --setuser ceph --setgroup ceph
restart nginx服务:
1sudo systemctl restart nginx
使用curl服务状态,如果出现下面的内容则服务正常:
1curl c1
2<?xml version="1.0" encoding="UTF-8"?><ListAllMyBucketsResult xmlns="http://s3.amazonaws.com/doc/2006-03-01/"><Owner><ID>anonymous</ID><DisplayName></DisplayName></Owner><Buckets></Buckets></ListAllMyBucketsResult>
使用radosgw-admin管理RGW #
创建S3用户 #
radosgw-admin是RGW服务的命令行管理工具。我们已经知道了RGW兼容绝大部分Amazon S3 API,下面我们先使用radosgw-admin来创建一个S3用户:
1radosgw-admin user create --uid=foo --display-name=foo [email protected]
2{
3 "user_id": "foo",
4 "display_name": "foo",
5 "email": "[email protected]",
6 "suspended": 0,
7 "max_buckets": 1000,
8 "auid": 0,
9 "subusers": [],
10 "keys": [
11 {
12 "user": "foo",
13 "access_key": "W0FE3UJ375EAHMT0660A",
14 "secret_key": "HeHbboOIfpc6N1lAxlCmW0S69owWBCBRQnL4BI6m"
15 }
16 ],
17 "swift_keys": [],
18 "caps": [],
19 "op_mask": "read, write, delete",
20 "default_placement": "",
21 "placement_tags": [],
22 "bucket_quota": {
23 "enabled": false,
24 "max_size_kb": -1,
25 "max_objects": -1
26 },
27 "user_quota": {
28 "enabled": false,
29 "max_size_kb": -1,
30 "max_objects": -1
31 },
32 "temp_url_keys": []
33}
注意到上面的命令输出中的access_key和secret_key:
1"user": "foo",
2"access_key": "W0FE3UJ375EAHMT0660A",
3"secret_key": "HeHbboOIfpc6N1lAxlCmW0S69owWBCBRQnL4BI6m"
使用S3 API需要使用access_key和secret_key。access_key用于标识客户端身份;secret_key作为私钥保存在客户端服务器,不会在网络中传输,通常用于作为计算请求签名的密钥。 使用access_key进行身份识别,使用secret_key进行签名,完成客户端的接入、认证和授权。
删除S3用户 #
1radosgw-admin user rm --uid=foo
使用Admin Ops REST接口管理RGW #
Admin OPERATIONS是RGW提供的一套REST接口,可以用来管理S3用户、Bucket、配额等信息,具体可查看ADMIN OPERATIONS。
为了使用这套接口,需要创建一个s3用户,并针对不同的接口赋予需要的权限。
这里创建一个admin用户:
1radosgw-admin user create --uid=admin --display-name=admin
2{
3 "user_id": "admin",
4 "display_name": "admin",
5 "email": "",
6 "suspended": 0,
7 "max_buckets": 1000,
8 "auid": 0,
9 "subusers": [],
10 "keys": [
11 {
12 "user": "admin",
13 "access_key": "IQDZQF92L8E9YT8YNUY3",
14 "secret_key": "BLUAVMwCMWGdINXXme6lETgjePqB8gcuYnJQ7XGN"
15 }
16 ],
17 "swift_keys": [],
18 "caps": [],
19 "op_mask": "read, write, delete",
20 "default_placement": "",
21 "placement_tags": [],
22 "bucket_quota": {
23 "enabled": false,
24 "max_size_kb": -1,
25 "max_objects": -1
26 },
27 "user_quota": {
28 "enabled": false,
29 "max_size_kb": -1,
30 "max_objects": -1
31 },
32 "temp_url_keys": []
33}
允许admin读写users信息:
1radosgw-admin caps add --uid=admin --caps="users=*"
允许admin读写所有的usage信息:
1radosgw-admin caps add --uid=admin --caps="usage=read,write"